
How to Use Men to Balance the Numbers of Women in Cyber Security.
I've got a bee in my bonnet and I feel compelled to write about this.…
thedigitaltransformationpeople.com


I've got a bee in my bonnet and I feel compelled to write about this.…
thedigitaltransformationpeople.com

Just recently both the UK and the USA have imposed a ban on laptops being…
thedigitaltransformationpeople.com

Researchers from Israeli Cyber Security Company Cybellum have discovered a zero day bug that impacts…
thedigitaltransformationpeople.com
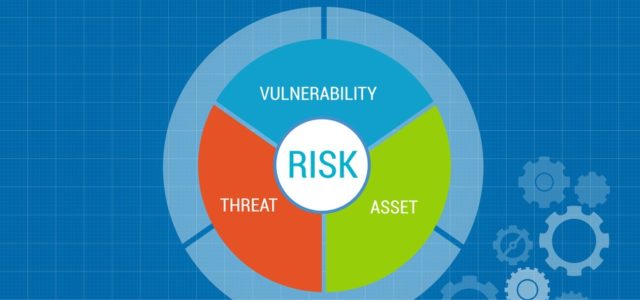
For companies getting serious about cybersecurity, a typical first recommended step is to obtain a…
thedigitaltransformationpeople.com

On Tuesday 7th of March 2017, WikiLeaks began its new series of leaks on the…
thedigitaltransformationpeople.com

7 real-life tips for cyber security practitioners and senior executives who want to look beyond…
thedigitaltransformationpeople.com

Working in cyber security for the last 19-years has been an amazing experience. Watching the…
thedigitaltransformationpeople.com

A Physical-Presence-on-the-Internet (Cyber PPI) access model is the first step to cyber security. Until this…
thedigitaltransformationpeople.com

As surely as the sun rising in the east, the state of cyber security can…
thedigitaltransformationpeople.com

A recent report stated there were over 4 billion breached records in 2016. This is…
thedigitaltransformationpeople.com

The Human Factor in Cyber Risk is the biggest cyber threat that businesses face today.…
thedigitaltransformationpeople.com

How does information security end up in the portfolio of the CIO?Historically, the CIO has…
thedigitaltransformationpeople.com