
Critical Takeaways from QNB Hack Incident
It has been identified by the security researchers that an SQL injection might have been…
thedigitaltransformationpeople.com


It has been identified by the security researchers that an SQL injection might have been…
thedigitaltransformationpeople.com
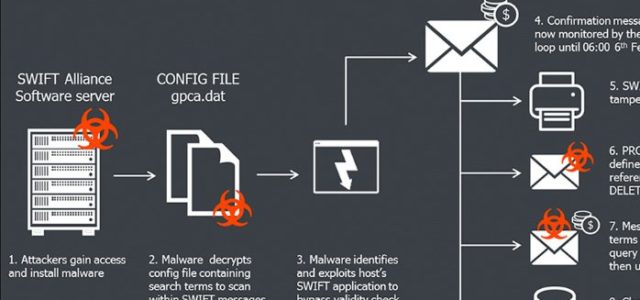
Finally by now the puzzle behind the Eighty Million USD Bangladesh Central Bank hack attempt,…
thedigitaltransformationpeople.com
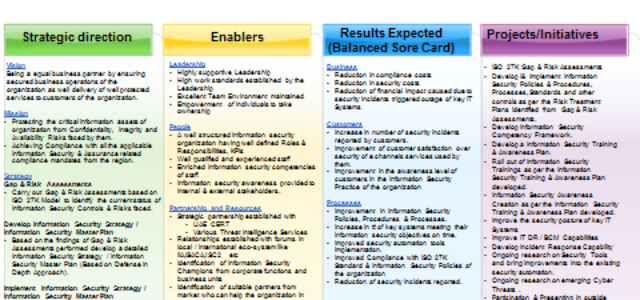
Why Information Security requires strategic planning? Strategic planning is the process that supports an organization…
thedigitaltransformationpeople.com

I am sure all of you have heard about the biggest data leak in the…
thedigitaltransformationpeople.com

IT Security may be modernising and becoming board-savvy, as IT did before it. But there…
thedigitaltransformationpeople.com

With recent high-profile information security breaches featuring some form of credential theft to enable abuse…
thedigitaltransformationpeople.com

When you and your friends gathered around your television in February for Super Bowl 50,…
thedigitaltransformationpeople.com

What keeps the CISO awake at night?In our latest GDS Video Snack from MeetTheBoss TV…
thedigitaltransformationpeople.com

A Checklist for controls to protect from Ransomware: Block access to websites with unwanted…
thedigitaltransformationpeople.com

I was happily ignorant about information risk , until very recently - when I got…
thedigitaltransformationpeople.com

What is RANSOMWARE? RANSOMWARE is a fast emerging dangerous malware that gets introduced into PCs and…
thedigitaltransformationpeople.com