
Data Ownership in a Digital World
Opaque Terms of Use around Data are making things worse. Recent years have been marked by…
thedigitaltransformationpeople.com


Opaque Terms of Use around Data are making things worse. Recent years have been marked by…
thedigitaltransformationpeople.com

We've all done it at some point, opened an attachment within a suspicious looking email…
thedigitaltransformationpeople.com

Today’s cyber risks come in all shapes and sizes, from disclosure of protected information due…
thedigitaltransformationpeople.com

For insurance company Chief Risk Officers, evolving and increasing cybersecurity risks are hard to ignore…
thedigitaltransformationpeople.com

Dealing with Shadow IT embodies the evolution of the role of the CIO, from being…
thedigitaltransformationpeople.com

I've got a bee in my bonnet and I feel compelled to write about this.…
thedigitaltransformationpeople.com

Just recently both the UK and the USA have imposed a ban on laptops being…
thedigitaltransformationpeople.com

Researchers from Israeli Cyber Security Company Cybellum have discovered a zero day bug that impacts…
thedigitaltransformationpeople.com
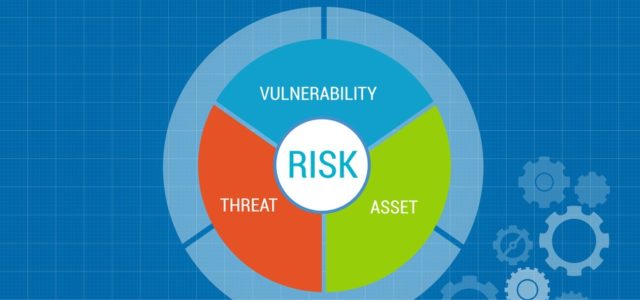
For companies getting serious about cybersecurity, a typical first recommended step is to obtain a…
thedigitaltransformationpeople.com

On Tuesday 7th of March 2017, WikiLeaks began its new series of leaks on the…
thedigitaltransformationpeople.com

Governance will always mean different things to different people. In small organisations, Governance tends to…
thedigitaltransformationpeople.com