
Physical Presence Technology – a complete explanation
The current cyber crisis is the result of a misapplication of technology based on a…
thedigitaltransformationpeople.com


The current cyber crisis is the result of a misapplication of technology based on a…
thedigitaltransformationpeople.com

Today’s method for Internet interaction was designed on the fly and built with limited knowledge…
thedigitaltransformationpeople.com

In Part 1, we introduced your face as the next computer cookie and discussed USA/UK retail…
thedigitaltransformationpeople.com

In Part 1, we introduced your face as the next computer cookie and discussed USA/UK retail…
thedigitaltransformationpeople.com

The traditional role of the CISO is changing. It is being challenged by emerging new…
thedigitaltransformationpeople.com

Simply throwing money at the problem is rarely the answer. Many CIOs and CISOs would…
thedigitaltransformationpeople.com
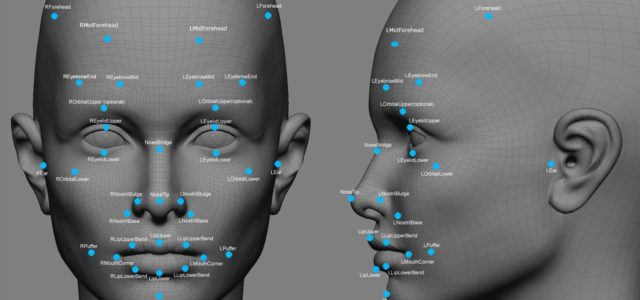
In Part 1 of this FaceID article series, we explored retail applications in USA / UK and…
thedigitaltransformationpeople.com

The Board of Governors of the Federal Reserve and the Federal Financial Institution Examination Council…
thedigitaltransformationpeople.com

With regards to many other C-level roles, the Chief Information Security Officer (CISO) position is…
thedigitaltransformationpeople.com

A serialized private portal is a unique operating environment that can be identified when it…
thedigitaltransformationpeople.com

Last century standards were presented to prevent cybercrime…but there was minimal theft and standards were…
thedigitaltransformationpeople.com